How to access OAuth 2.0 protected APIs
Get Started
1. The Web Page Requests Users Authorization From Google

https://accounts.google.com/o/oauth2/v2/auth/. Based on the offical documenation, the request should include the following parameters:| parameter | Description |
|---|---|
| client_id | Required, The client ID for your application. You can find this value in the API Console Credentials page. |
| redirect_uri | Required, Determines where the API server redirects the user after the user completes the authorization flow. The value must exactly match one of the authorized redirect URIs for the OAuth 2.0 client, which you configured in your client's API Console Credentials page. |
| response_type | Required, Determines whether the Google OAuth 2.0 endpoint returns an authorization code. Set the parameter value to code for web server applications. |
| scope | Required, A space-delimited list of scopes that identify the resources that your application could access on the user's behalf. These values inform the consent screen that Google displays to the user. |
| access_type | Recommended, Indicates whether your application can refresh access tokens when the user is not present at the browser. Valid parameter values are online, which is the default value, and offline. |
| state | Recommended, Specifies any string value that your application uses to maintain state between your authorization request and the authorization server's response. |
INFO
2. User Authorizes the Application
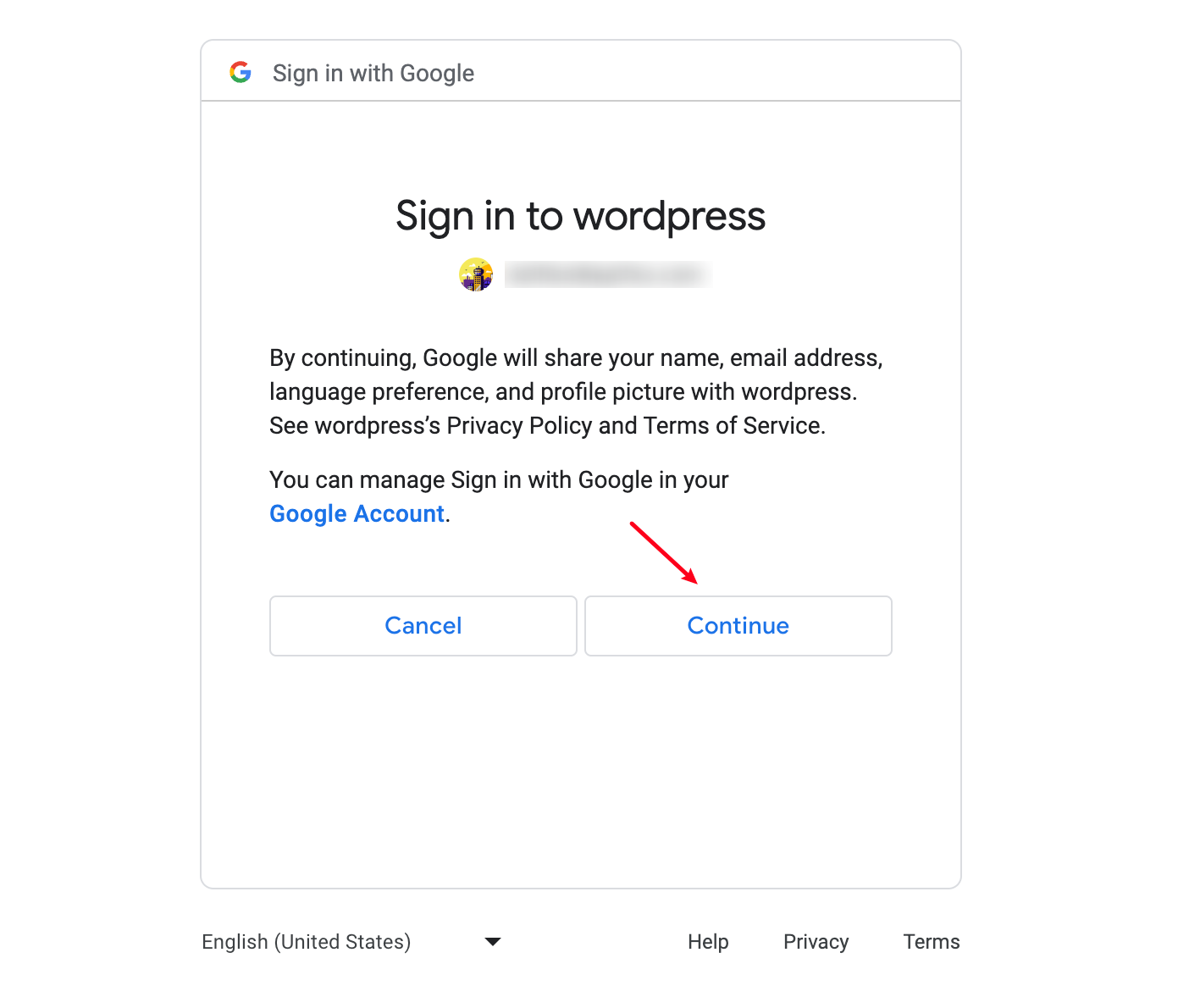
3. The Web Page Requests an Access Token from Google
# Error
http://example.com/#error=access_denied&state=state_parameter_passthrough_value
# Success
http://example.com/#state=state_parameter_passthrough_value&access_token=***&token_type=Bearer&expires_in=***&scope=email%20https://www.googleapis.com/auth/userinfo.email%20openid&authuser=0&prompt=consent4. Sending the Access Token to Get Information from Google APIs

5. Google Confirms the Access Token

picture and email. The website can use this data to automatically display the user's profile picture and email address, eliminating the need for manual entry.Conclusion
References
1.
2.
Modified at 2024-08-29 03:22:56